Against a backdrop of digital transformation, the challenges of data security are considerable. What on the one hand is a necessity for modernization, a competitive advantage or a feature of economic development also appears to be a source of vulnerability if systems and data are not well protected.
Security plays a decisive role in all fund-raising and investment activities. Without it, major incidents could impact asset managers and their businesses.
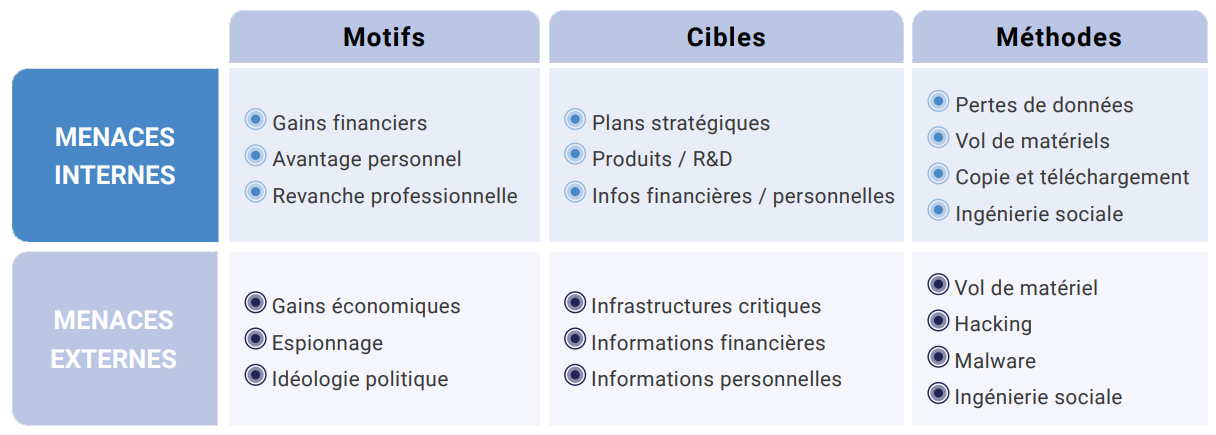
New risks threaten data security
Against a backdrop of ever-increasing threats, the risk of data breaches is almost constant, and regulatory requirements are becoming ever more stringent: virus injection, theft of customer data, intrusions, increased attacks linked to teleworking (Covid-19 crisis), industrial espionage...
According to a report by the World Economic Forum, cyber risk has increased the most with the Covid-19 crisis and the rise of online commerce. It is estimated at $6,000 billion in 2021. This figure is expected to reach $10,500 billion in 2025, representing growth of almost 15% per year 5. There were an average of 270 attacks per organization in 2021, up 31% on 2020.
Alternative investment players need to protect several types of data:
- Investor data: personal data, KYC documents, transactions, valuation, holdings, amount committed and invested in each fund and portfolio,
- Information about the management company and the funds under management,
- Portfolio data: deals in progress, companies purchased, funds invested, cash flow invested, valuation, portfolio KPIs, etc.
- Fund and portfolio performance data,
- Fund managers' personal data, carried data...
Our tips for securing your data
All data, whether structured or unstructured, must be secured. We recommend :
- Enforce a global security policy for front, middle and back office information systems,
- Introduce classification coding at the level of each data typology,
- Exclude highly sensitive data from the platform by anonymizing, pseudonymizing or encrypting data,
- Define a strict data classification policy based on regulatory constraints and the sensitivity of our businesses to personal data.
The challenges facing companies
Cybersecurity challenges facing alternative investment players :
- Audit and implement data transformation rules (data lineage): identify data origins and uses, define rules and life cycle.
- Authenticate: be able to geolocate data, ensure the security of data transmitted by the supplier, guarantee service availability.
- Protecting data: ensuring compliance with the RGPD by protecting sensitive data, defining and managing authorizations and data retention periods.
- Managing authorizations: managing consent and the right to be forgotten, data masking and anonymization.
Characteristics of optimum access management
Optimal access management must be :
- Simple and understandable, with a vision of the users and the uses brought about by a "user-friendly" tool,
- Integrated across the data platform and then specifically for each new application,
- Automated as soon as possible,
- Delegate to business lines and functional teams,
- Regulated by an appropriate definition of access rights and traceability.
Secure data transfer and storage
Two risks in particular concern asset managers: data transfer and cloud storage solutions. Many companies are choosing to host their tools in the cloud, which is now becoming the norm and the future of IT. The cloud market is booming (new products, busy vendor roadmaps, mergers/acquisitions, partnerships, etc.).
When selecting third-party IT service providers, it is important to obtain detailed information on their security programs: access to data, location (country of competent jurisdiction), right to audit, technical aspects of the infrastructure and measures taken by the provider to ensure the integrity and security of this data, etc.
The cloud to meet IT and business needs.
According to a Gartner study, 80% of companies will have closed their traditional data centers by 2025. This statistic demonstrates that building architectures in the cloud is becoming widespread. This trend is confirmed by a study of the cloud provider market, which is highly dynamic and constantly evolving. It offers a wide variety of solutions and service catalogs.
There are several reasons for this growing success. Cloud solutions enable companies to scale their platform capacities to suit their specific use cases, offering unlimited flexibility and agility. All testing phases are exempt from heavy and risky investment in on-premise hardware, and are therefore greatly facilitated. There's no longer any need to acquire expensive hardware for testing. The same applies to the scalability and modularity of the platform, which can be adapted to each use case, by adapting architectures, SLAs and so on.
What's more, the differentiation between storage and cloud services brings a great deal of cost control. If your use cases involve stakeholders based in distant geographical locations, the use of cloud services makes it possible to build a distributed architecture that will bring the workload closer to users and reduce latency. The resulting efficiency, scalability and speed will boost end-user adoption rates and secure project ROI.
Cloud solution providers support compliance. The technical foundations offered by cloud operators meet a number of prerequisites. It is possible to design a solution in a receptacle that already has an up-to-date level of compliance and security. Suppliers ensure platform security and compliance with changing data regulations. This saves time, process and budget.
Conclusion
Cybersecurity, data security and respect for personal data are of vital importance to asset managers, investors and fund administrators. To best ensure the security of its data, every organization must first and foremost inform and sensitize its employees to these risks, their sources and their potential impact, and provide them with the means to identify and avoid them. This can be achieved by organizing workshops and in-house training courses, in collaboration with the IT department, or with the support of a specialist firm such as AssetValue Consulting.
